An Overview on Authentication and Smart Cards Administrators have to secure the network from attacks launched by hackers, spies, terrorists, thieves and criminals. Security encompasses numerous technologies, protocols, standards, policies, passwords, and secret keys. All these mechanisms typically focus on the following: Authentication Access Control Data Protection Auditing/Accountability Authentication is the process by which an entity identifies itself, before network logon is permitted. After a user is authenticated, access control defines what resources can be accessed, what actions can be performed on the resource, and whether these actions are audited Read More
How to Copy DVD Movies
Movie lovers may like a movie on a DVD and want to copy it to a blank DVD to save the cost of buying the original DVD. With the help of DVD burning software such as DVD ripper, copying a DVD is possible. Most DVD ripper software is shareware, which means that it can be tried for free for a limited period, after which the user must pay for the full version. DVD Software for Conversion Software like Clone DVD can copy DVD movies with a single click. Users can Read More
IVR (Interactive Voice Response)
IVR (Interactive Voice Response) allows a computer to interpret the speech of a human being as input to the system. Similar to a touch tone system that listens to the unique sound of each button press a user makes, the IVR system analyzes the sound of the user speaking and converts the user's speech to a format it can interpret. Like a traditional touch tone system, the user navigates the computer system by making menu selections or responding to requests for other, more complex input. With Interactive Voice Response systems, Read More
Standard Library Functions
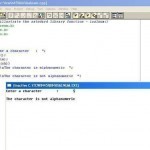
A library is a collection of programs and functions which can be used by other programs. Like all other high-level languages, C++ provides function libraries containing built-In functions. These standard functions are extremely useful to the programmers. The advantages of library functions are listed below: Reusability of code : The program development activity requires three major activities: coding, testing and debugging. If a function is developed previously, then it is available as a standard library function and the effort of redevelopment can be avoided. Faster development : Since many useful Read More
How to Read Windows Log Files
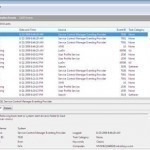
Reading Windows log files is an important part of maintaining proper operation and ensuring system security. In addition, log files can be extremely useful in troubleshooting Windows errors. Only a Windows Administrator can read some Windows log files, such as the Security Event Log. Any system user can view other log files, such as logs that software applications created. Each log contains a list of events that occurred, along with problems, failures, and warnings. How to Read the Windows Application, Security, and Sytem Log Files The Windows application, security, and Read More
Amp (Ampere)
The ampere, amp for short, is the standard unit of electrical current. It is defined as the current required to produce a certain force between two parallel and infinitely long wires separated by one meter. According to Ohm’s law, one ampere of current is produced when one volt of potential difference exists across a conductor with one ohm of resistance. One ampere is also equal to the flow of one coulomb of electric charge per second. History of the Amp The ampere was defined at an international conference in 1881, Read More
Picasa for Mac
Picasa is a slideshow software, much like Microsoft PowerPoint, that Google provides for its users at no charge. Picasa is designed for editing and assembling photos and videos into slideshows, presentations, and simple albums that will be stored on external media devices or uploaded to the Internet, which Picasa is able to do. While Picasa was once withheld from Mac users who were forced to use iPhoto (a Mac alternative), with a Picasa plug-in, Picasa is now available on multiple platforms including Mac. Picasa for Mac Picasa for Mac Read More
Bad_Pool_Header
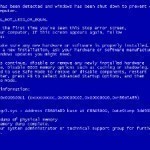
One of the most famous fatal errors that occurs on computers running the Windows Operating System (OS) is the Blue Screen of Death (BSOD). A BSOD may be the result of a number of problems including hardware, software, or driver incompatibility with the computer’s OS. The BSOD often prevents users from rebooting their computer or using it normally. One common BSOD error that occurs is the Bad_Pool_Header. When this error occurs, the OS will not load and users will not be able to access the information stored on the NTFS Read More
EMF Meters

An EMF meter detects and measures an electromagnetic field. There are many types of EMF meters and they have many uses, including ghost hunting. Most EMF meters are “AC EMF meters” and can only detect the rate of change in an oscillating magnetic field. However, commercial grade EMF meters that can detect specific electromagnetic frequency ranges are available. While any EMF meter is generally capable of taking accurate measurements of most electromagnetic fields, the user should do research before purchasing an EMF meter for any specific project, experiment, or task. Read More
C++ Tutorials
C++ Tutorials C++ is a programming language that is demand these days. It’s being implemented on a wide range of hardware and OS or platforms. It is indeed an efficient compiler to native code, which is why many people want to learn more about it. Here in our C++ Tutorials page, you will learn the basics and everything you need to know about C++. Break and Continue Statements A tutorial that tells about Break and Continue Statements in C++. Goto Statement A tutorial that tells about goto Statement in C++. Read More


Share on: