Metal detector technology has been used for a number of decades to locate various metallic artifacts and precious metallic ores. An uncommon, but accurate metal detector is the Pulse Induction Metal Detector. It uses Pulse Induction Technology to find metals. What is Pulse Induction Technology? In Pulse Induction technology, a coil is used as a transmitter and receiver. Pulse Induction metal detectors are likely to have a single coil, but there are others that have additional coils. Powerful pulses of current are sent through the coil. The pulses create magnetic Read More
Interactive TV
Interactive TV is when the viewer and broadcaster can communicate with each other, usually in real time. Normal TV flows in a one way path, from the broadcaster to the viewer, however interactive TV, usually includes a digital modem or other form of hardware that can return information or data from the viewer back to the broadcaster which can include either the cable operator, satellite TV operator or broadcast company. Interactive TV sometimes referred to as iTV has been growing in popularity and today with new innovations in technology is Read More
How Does the Email System Work?
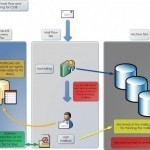
Millions of people all over the world use email every day but not too many of them really understand how email works. Between browsers, email clients, email addresses, servers, and ports, it is easy to see how many people are confused by the email system or simply do not care to learn about it. For those who do care, however, we have created this article for you to learn how email works without having to sort out complicated information. Browser Email The most common way of accessing email is through Read More
How to Change a Facebook Password
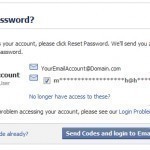
Changing one’s password is a practice that can help prevent unauthorized access to one’s Facebook account. A periodic password change is recommended, especially if one signs into the account through different devices or have experienced any form of account activity that one has not personally authorized or posted. Changing one’s password can help to remove this accessibility from others as well as protect one’s account from being compromised in the future. To change one’s current Facebook password, follow these directions: Note: Sign into one’s Facebook account with a computer to Read More
Limonene
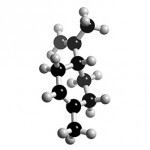
One of the primary components of the oil that is extracted from the rind of citrus fruits is Limonene. When the juice is removed from a citrus fruit, the oil is also extracted from the rind, separate from the juice. The oil is then distilled so that flavor and other fragrance compounds can be removed from it. After this process is complete, the left over oil is called limonene or food-grade limonene. After the juicing process is completed, the peels are placed in steam extractors in order to harvest additional Read More
How Do I Configure My RCA DirectTV Remote?
To configure your RCA DirectTV remote, you need to have the receiver's brand and model number. This can either be found within the instruction manual or it can be found on the back or the bottom of the box. Write this down so you don't have to keep going back to the box to get the digits. Put the box back where you want it and plug it in so that it can begin powering up. Now that you've got the brand of the receiver, go into the instruction manual Read More
How to Block Incoming Calls
Service Provider If a user is being harassed by unwanted or threatening phone calls, the first thing he/she needs to do is contact his/her service provider. The service provider will then tell the user what to do and inform them about the various methods of blocking unwanted calls. The service provider may also block the unwanted call or block all incoming calls until a solution is found. Also, if a user is receiving threatening calls, the service provider can contact the authorities and possibly assist in locating the caller/pressing charges Read More
How to Connect Multiple Monitors to Your Laptop
Many computer owners find the multiple monitor features extremely useful. The multiple monitor feature has been around for many years and is available on Macintosh computers, Linux computers and Windows Operating systems- specifically on Windows 98, ME, XP, and Vista. It is quite easy to add one or more monitor to your computer, however there are generally only two modes available. They are Mirror Mode and the Multi Monitor Mode. Mirror Mode The first mode is called the mirror mode. In mirror mode, the second monitor you add will be Read More
Virtual Base Classes
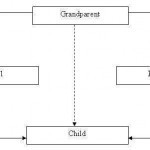
A situation may arise where all the three kinds of inheritance, namely, multilevel, multiple and hierarchical inheritance are involved. This is illustrated in the figure below; the child has two direct base classes 'parent1' and 'parent2' which themselves have a common base class 'grandparent'. The 'child' inherits the traits of grandparent class via two separate paths. It can also inherit directly, as shown by the dotted lines. The grandparent class is sometimes referred to as indirect base class. Such inheritance by the child class may create some problems. All the Read More
ATSC Tuner
An ATSC tuner is a device that is used in the reception of digital TV signals (DTV), including HDTV (High Definition TV) signals. An ATSC tuner is specifically used by broadcast television stations in North America to send their over the air TV signals to homes that have a television with either an internal ATSC tuner or an external ATSC tuner in the form of a set top box. Although the term "ATSC tuner" is used by most commercial products, scientifically, it is actually referred to as an "ATSC receiver". Read More


Share on: