Wireless routers are network devices that combine the functionalities of a router and a wireless access point. Wireless routers can be connected to broadband modems to provide wireless access to the Internet to two or more computers or laptops within a home environment. They enable greater mobility for laptops and other portable computers. They can also operate in a wired LAN (Local Area Network) or wireless LAN network. Some wireless routers have built in modems as well. Wireless routers are secure as they act as a hardware firewall. They provide Read More
What is a Fullerene?

A fullerene is a third form of the carbon molecule that falls in between graphite and diamond. It was named for Richard Buckminster Fuller, who was well known for geodesic dome designs whose appearance closely resembled spherical fullerenes. A Fullerene’s carbon atoms may be arranged in a cylindrical, ellipsoid, or spherical form. The spherical fullerenes are called “Buckyballs,” while the cylindrical ones are known as “Buckytubes” or “nanotubes.” When were Fullerenes Discovered? A group of researchers discovered fullerenes at Rice University while they were conducting laser spectroscopy experiments in September, Read More
Implementing Folder Redirection with Group Policy
An Overview on Folder Redirection Folder Redirection is a Group Policy feature that enables users to redirect the system folders containing the profile of a user on the network, through the use of the Folder Redirection node in the Group Policy Object Editor console. This basically makes folder redirection a user configuration option. Through the use of the Folder Redirection feature, users can configure that the system folders’ contents on the user remains the same, irrespective of the particular computer used to log onto the system. The system folders that Read More
How to Uninstall Vista
Although Vista is the most recent and technologically advanced operating system available from Microsoft, many users still consider Windows XP or other operating systems more stable. One of the reasons that many end users who have Windows Vista loaded onto their computer want to uninstall it is that many computers just are not powerful enough or configured properly to take advantage of all of Vista’s features. Uninstalling Vista is, in most cases, a fairly simple process. The process takes about an hour or two. Here are some tips. There are Read More
Abandonware

Any game or software, which is no longer supported by its owner or publisher, is described as abandonware. This indicates that the owner of the game or software has abandoned their product because they no longer yield profit from them. There are several abandonware sites, which are conceived as illegitimate, unless the owner of the software has relinquished them as freeware. Generally, abandonware software is not commercially supported, as the copyright ownership might be imprecise for several reasons. Though abandonware software is not legally marketed, they could be obtained by Read More
Doubly Linked List – Traversing and Search
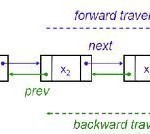
Traversing a Doubly Linked List A doubly linked list can be traversed either way and that too very conveniently. Inorder traversal Reverse order traversal Inorder Traversal To traverse the doubly linked list, we walk the list from the beginning, and process each element until we reach the last element. .cf { font-family: Lucida Console; font-size: 9pt; color: black; background: white; } .cl { margin: 0px; } .cb1 { color: green; } .cb2 { color: blue; } .cb3 { color: maroon; } void traverseinorder(node *head) { while(head!=NULL) { printf(“%dn”,head->info); head=head->next; Read More
How Wave Power Works
Wave power involves the ability to harness the power of the ocean's waves and use that power to generate electricity or do other types of useful work. Much like solar power, geothermal power, and wind power, wave power is known as a type of renewable energy source because nothing is consumed in the process. Also, wave power is often confused with tidal power, another type of power which is generated via the ocean. While wave power uses the actual surface waves which form in the ocean, tidal power takes advantage Read More
Noise Pollution
Noise pollution refers to the excessive, upsetting, and disruptive noise that machines or animals create. Aircraft, rail, automobiles, and construction sites cause the most noise pollution. Noise pollution occurs both indoors and outdoors. Other sources of noise pollution include fireworks, air horns, dogs, audio equipment, mechanical equipment, building or car alarms, and appliances. Noise pollution was largely ignored until the mid-1970's when the government started placing regulations on industries that significantly contributed to noise pollution. What Are the Effects of Noise Pollution on Human Health? Noise pollution can have a Read More
Linux Restricted Shell
The idea of a restricted shell first arose in the Unix operating system in order to prevent the end-user from doing as many operations as a normal shell allows. A restricted shell lets the administrator control the end-user’s computing environment by only permitting explicitly used commands to be used. The Linux restricted shell (rssh) is similar, but only a minimum command set is enabled for the end-user. When installed, the default configuration is to remove all access and capabilities until the configuration file is modified by the admin. In the Read More
Ntoskrnl.exe is Missing or Corrupt
The NTOSKRNL.EXE is missing or corrupt error message is usually encountered during the boot process of NT based Windows operating systems. It can also be classified as a blue screen error, which is a colloquial term coined by users to describe error screens displayed by Windows. These errors are displayed due to critical system errors which may cause the system to shutdown to avoid system damage. This specific error may occur because of common hardware failure, the Ntoskrnl.exe file is missing or corrupt, Windows is not installed in the location Read More


Share on: