In Windows Vista, there is a difference between accounts with “computer administrator” privileges and the Administrator account. In the Administrator account, the User Account Control is disabled. Also, the Administrator account is present, but hidden and disabled by default. Please be aware that Vista Beta 2 has a bug that may cause big problems, if a password is created for the Administrator account in Computer Management. Enabling the Windows Vista Administrator Account Here are two methods that will teach the user how to enable the Windows Vista Administrator Account. Method Read More
Apple TV Alternatives

Apple TV is one of the available options for streaming and Internet based entertainment for the television. It has an extensive library of content when paired with Apple iTunes. Although Apple TV can be an affordable option, the device has many limitations that really reduces it to a basic streaming device. This device is not the only one of its kind to provide streaming and entertainment capabilities. There are many options to choose from with varying degrees of quality and selection. The following are some of the best digital media Read More
Learning Management System
Learning Management Systems (LMSs) are software programs that are used to centrally administer classroom education or training events via the Internet. High end LMS applications are normally capable of providing a wide-range of management and education-related services. These services range from personalizing content for the student, supporting web standards and portability, delivering content in a rapid fashion, supporting self-guided or self-paced courses of instruction, and providing centralized administrative controls over the course content. What Are Learning Management Systems Used For? An LMS can be used for many training or education Read More
How an LCD TV Works

From the wordings of the name, an LCD TV is a short form of Liquid Crystal Display Television. What is presented in an LCD TV to make it work the way we see it is founded on the special effects of substances of light and liquid crystals acting on each other. These are brought together through a technical process known as Thin Film Transistor. Keep in mind that this process has witnessed a lot of innovations over the years to bring the LCD TV to what we have today. The Read More
ROT-13
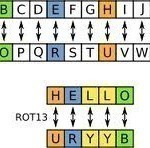
ROT-13 is a simple substitution cipher used to obfuscate Usenet posts. ROT-13 is not meant for use as a data encryption cipher. ROT-13 is so named because every character is rotated 13 places. ROT-13 “Encryption” Chart Plaintext A B C D E F G H I J K L M N O P Q R S T U V W X Y Z Ciphertext N O P Q R S T U V W X Y Z A B C D E F G H I J K L M Read More
JPEG
JPEG (Joint Photographic Experts Group) is a lossy compression technique for color pictures. Pronounced "jay-peg", JPEG is an ISO/IEC group of experts that creates and maintains standards for a suite of compression algorithm for computer image files. JPEG standards help image files to be compressed to around five percent of their original size, though some details are lost during compression. The commonly used file extensions for th JPEG format are .jpg, .jpeg, .jfif, .or jpe. The extension JPEG specifies only how an image is transformed into a stream of bytes. Read More
Specific Gravity
Specific gravity is a special case of relative density. That is, a substance’s density is divided by the density of water at 4 F (0 C). Since water has a density of 1 gram/cm3 and all of the units cancel, specific gravity is the same number as density, but without any units (dimensionless). Relative density is another dimensionless number that measures any substance’s density in relation to another. A relative density greater than 1 (one) means that the substance in the numerator has a bigger density than the one in Read More
Understanding and Managing SMTP Virtual Servers
Simple Mail Transfer Protocol (SMTP) Service Overview The Simple Mail Transfer Protocol (SMTP) service, a primary service included as part of IIS, performs the key functions and has the characteristics listed below: SMTP can be used to forward mail from one SMTP host to another. SMTP cannot deliver mail directly to the client. Mail clients use POP3 or IMAP to receive e-mail. Windows Server 2003 includes the POP3 service for providing clients with mailboxes and for handling incoming e-mail. It enables IIS machines to operate as SMTP hosts to forward Read More
Cryptographic Libraries

Cryptography is very difficult. It is even more difficult to tell if you have done it correctly. If you design and implement your own cryptographic algorithm, the odds are that you will fail to create a secure system. It is much better to code your application to use an existing cryptographic library which has been tested with extensive peer review. Adam Shostack maintains a good list of cryptographic libraries at Source Available Cryptographic Libraries. PCL is an interesting cryptanalysis library with functions for dictionary attacks and brute force attacks.
GPS Jammer

GPS stands for Global Positioning System. It is used by individuals, commercial entities and the military for navigational purposes. GPS uses 24 satellites that orbit the earth and send radio signals. The GPS satellites work with a GPS receiver which today can be found in individual handheld units, car navigational systems, boat navigational systems, highly precise commercial products and a wide range of military equipment. Operation of GPS GPS operates using triangulation. Triangulation is a method in which three separate points are measured to calculate location. For instance, in a Read More


Share on: