Configuring VPN Connectivity Virtual Private Networks (VPNs) provide secure and advanced connections through a non-secure network by providing data privacy. Private data is secure in a public environment. Remote access VPNs provides a common environment where many different sources such as intermediaries, clients and off-site employees can access information via web browsers or email. Many companies supply their own VPN connections via the Internet. Through their Internet Service Providers (ISPs), remote users running VPN client software are assured private access in a publicly shared environment. By using analog, ISDN, DSL, Read More
Active-X
Active X is the name for a selection of object-oriented tools and programming technologies that were developed by Microsoft. From time to time, new versions of Active X have been released to provide support to the ever widening array of applications that are used in the home and the workplace. Active X can have an impact on applications that run quietly in the background, as well as applications that are used for online communications. What are the basic components of Active X? The single key tool within Active X is Read More
Global Catalog
The global catalog is a distributed data repository that is stored in global catalog servers and issued via multimaster replication. It basically is composed of a representation (partial) of every object in the multidomain Active Directory forest that can also be searched. The global catalog is used because searches can be made faster because they don't need to go through the hassle of involving referrals to different domain controllers. In addition, the global catalog allows finding an object that you wish without needing to know the object's domain name. This Read More
Replication Topology in Active Directory
Replication Topology is the route by which replication data travels throughout a network. Replication occurs between two domain controllers at a time. Over time, replication synchronizes information in Active Directory for an entire forest of domain controllers. To create a replication topology active directory must determine which domain controller's replicate data with other domain controllers. The Knowledge Consistency Checker (KCC) is a built-in process that runs on each domain controller and regenerates the replication topology for all directory partitions that are contained on that domain controller. The KCC runs at Read More
DFS (Distributed File System)
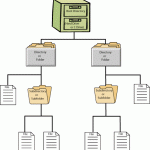
DFS (Distributed File System) provides a mechanism for administrators to create logical views of folders and files, regardless of where those files are physically located on the network. DFS also allows administrators to distribute shared folders and work loads across several servers for more efficient network and server resources use. Fault tolerance network storage resources are also available by using DFS. DFS is a service that provides a single point of reference and a logical tree structure for file system resources that may be physically located anywhere on the network. Read More
How to Recover a Boot Record in XP
The boot record stores the first bits of software that the system executes once the BIOS hands control of the computer over to software. The boot record stores instructions used to start Windows XP. Each drive partition can store a boot record. Damage to a boot record may be caused by a hardware error, software error, user error, or even malware such as a boot sector virus. How to Recover a Boot Record in XP To recover the boot record in XP, use the fixboot command in the Recovery Console. Read More
Installing ISA Server
Modifying the Local Address Table (LAT) for ISA Server Installation When ISA Server runs as a firewall (install ISA Server in Firewall mode or in Integrated mode), ISA Server uses the Local Address Table (LAT) to determine the following information so that it can implement access rules: Determine the IP addresses on the private network. Determine the IP addresses on the public network. The firewall client uses the information in the LAT to determine the following: The addresses that need to be forwarded to the firewall The addresses which should Read More
How to Improve Computer Speed

A registry cleaner is a program that cleans registries. A registry is a collection of essential computer files that allows the operating system to run properly and access various files and programs on the computer. When missing files, files with the same name or content, or files that cannot be accessed corrupt the registry, the computer’s performance and speed may be negatively affected. By simply running a registry cleaner, such as CCleaner, the user can dramatically increase his/her computer’s speed. What is a Defragmenter? A defragmenter is a program that Read More
How to Unprotect an Excel Sheet
Unprotecting an Excel sheet is surprisingly easy. If your Excel sheet is password protected and you do not know the password, there is no way that you can unprotect the sheet in that particular workbook – but you can create a new workbook which will contain exactly the same formulas, formatting and values that will not be protected and will be editable. How to Unprotect a Non-Password Protected Excel Sheet Open up the Excel document. Click on the “Review” tab. Click “Unprotect Sheet” or “Unprotect Workbook.” How to Unprotect a Read More
Securing Database Servers
Database Server Security Overview When it comes to securing database servers, the actual database software usually provides some security features or mechanism which you can implement. A common database is Microsoft SQL Server which you can manage through its Enterprise Manager tool. The Enterprise Manager can be found in the SQL Server program group. It is recommended that you do not expose your SQL Server databases to public networks such as the Internet. If you do have to connect a SQL Server database to the Internet, a firewall should be Read More


Share on: