ISA Server Client Types Overview The different ISA Server client types are: Firewall client: These are client computers on which Firewall Client software is installed and enabled. SecureNAT client: These are client computers that have no Firewall Client software installed and enabled. Web Proxy client: These are client Web applications which are set up to use the ISA Server computer. You have to consider the needs of the organization before you install any client software: You have to determine which applications and services your internal clients need to access. You Read More
What is a GPT Protective Partition?
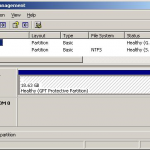
A GPT protective partition is a partition on a hard drive that a GUID Partition Table protects. A partition is a continuous area of storage space on a hard drive that is separated from the rest of the hard drive and acts as its own storage device. A GPT protective partition cannot be deleted or reformatted, but can be much larger than partitions that the Master Boot Records (MBR) generate. GPT protective partitions arise from creating partitions on a hard drive that GPT manages. While GPT protective partitions are useful Read More
Monitoring Exchange Server 2003
Monitoring Exchange Server 2003 Server Daily To ensure that your Exchange Server 2003 environment is operating and operating optimally, you have to monitor your Exchange Server 2003 server services daily. You have to monitor performance, and recognize and eliminate bottlenecks if you want to have a system that is optimized. You can use System Monitor, Task Monitor, Network Monitor, Event Viewer, and Performance Logs And Alerts to monitor the system. You can use System Monitor and Performance Logs And Alerts to create baselines, identify bottlenecks, determine performance trends, and test Read More
How Do I Uninstall Windows Live Messenger?
Windows Live Messenger is an instant messenger program that comes previously installed on computers that shipped with Windows as the operating system. In most cases, people use a different instant messenger program and would like to remove this software from their computers. Removal, though, can be tricky because it is not as simple as doing a program uninstall. That's only the first step. Open the Control Panel and click the Programs and Features button. This will take you to a list of all the programs that are on the computer. Read More
Configuring the Software Metering SMS Feature
Configuring Software Metering The components involved in the software metering process: Site server: This is the place where you configure the components that support software metering, and specify which applications are included or excluded from the software metering process. The site server is also where you specify how many licenses are available, and the balancing of license information. Software metering server: The software metering server performs the following functions: Obtains configuration information from the site server. Obtains license information from the site server. Maintains and stores software usage information received Read More
How to Delegate Administrator Privileges in Active Directory
The primary reason to create organizational units is to distribute administrative tasks across the organization by delegating administrative control to other administrators. Delegation is especially important when a decentralized administrative model is developed. Delegation of administration is the process of decentralizing the responsibility for managing organizational units from a central administrator to other administrators. The ability to establish access to individual organizational units is an important security feature in Active Directory. Users can control access to the lowest level of an organization without having to create many active directory domains. Read More
How to Auto-Hide the Taskbar with the Registry
One way to modify a Windows desktop’s look is to auto-hide the taskbar. The auto-hide option modifies a desktop by giving the user some extra space. When using the auto-hide taskbar option, the taskbar disappears when it is not being used. However, whenever it is required, simply place the cursor at the bottom of the screen (where the taskbar would normally be) and it will appear. There are two main ways to auto-hide a taskbar, one is by using the registry and the other is to make changes to the Read More
Windows Media Player Error 0xc00d1199
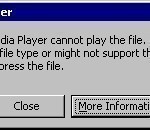
Windows Media Player develops a variety of errors when invalid changes are made to the program itself or the computer system in use. The Error code “0xc00d1199 – Cannot Play File” is a common error that occurs for a variety of reasons. Note: Clicking on “More Information” provides details about the error code. Installing Codec Information One of the reasons that a file may not be playable is the lack of the proper codec to decode the information in the file. The appropriate remedy is to install the correct codec Read More
Active Directory
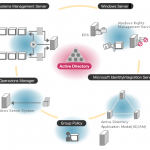
Active Directory (AD) is a structure used on computers and servers running the Microsoft Windows operating system (OS). AD is used to store network, domain, and user information and was originally created by Microsoft in 1996. It was first deployed on Microsoft Windows 2000. Active directories provide a number of functions to include providing information regarding objects optimized for fast access and / or retrieval. This allows administrators to setup security, push computer updates, and acts as a hierarchical structure. The structure is normally configured in three categories to include: Read More
Implementing NWLink

NWLink Overview NWLink IPX/SPX is the Microsoft implementation of Novell’s NetWare Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX) protocol. NWLink IPX/SPX is simply called NWLink. NWLink is used in Novell NetWare, and can be considered IPX for Windows. NWLink is an IPX/SPX compatible transport protocol that was developed to enable Windows 2000 computers to communicate with NetWare services. It is therefore used when clients running Microsoft operating systems (OSs) need to access resources on NetWare servers. It is also used where clients running NetWare need to access resources on computers running Read More


Share on: