Recursion is an ability of a program to call itself, either directly or indirectly. Its a programming technique that naturally implements the divide and conquers programming approach. It does the task of calling itself. To do this, it must reduce its size upon every call; else, the process will become infinite. Type of Recursion Direct Recursion Indirect Recursion Example: To compute factorial of a number The above program works as follows, fact(5) = {if(5= =1) is false thus return 5* fact (4)} fact(4) = {if(4= =1) is false thus return Read More
Java Loops – For, While, and Do
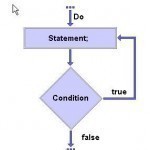
Java supports three types of loops: For, While, and Do. The Java For Loop The Java for loop is a looping construct which continually executes a block of statements over range of values. Java for Loop Syntax The syntax of a for loop in Java is: for (initialization; termination; increment) { statement } Example Java for Loop Here is a Java for loop which prints the numbers 1 through 10. for (int loopvar = 1; loopvar <= 10 ; loopvar++) { System.out.println(loopvar); } The Java While Loop A Java while Read More
How Do I Enable Javascript on My Computer?
To promote a better experience on different websites, owners of these websites use JavaScript. However, there are instances where JavaScript gets disabled and some of the different components on the site can't be experienced because of this. Enabling JavaScript is different for each web browser, but all of it takes about a minute to complete. Once you're done, simply restart the browser and JavaScript will be enabled. Enabling JavaScript on Internet Explorer To enable JavaScript on Internet Explorer, go to the top and click tools. Then click Internet Options. For Read More
Address Calculation Sort
In this method, a function fn() is applied to each key. The result of this function determines into which of the several sub-files the record is to be placed. The function should have the property that x <= y, fn (x) <= fn (y). Such a function is called order preserving. Thus all of the records in one sub-file will have keys that are less than or equal to the keys of the records in another sub-file. An item is placed into a sub-file in correct sequence by using any Read More
Random Number Vulnerability
Computers are deterministic and are therefore predictable. Computers cannot, in and of themselves, generate truly random numbers. In the absence of outside input, computers can only create pseudo-random numbers. In the words of John Von Neumann, “Anyone attempting to produce random numbers by purely arithmetic means is, of course, in a state of sin.” A random number vulnerability occurs when a program uses a method of generating random numbers which is either: Not random Predictable To generate good random numbers, the computer must have two things: A good random number Read More
Sorting
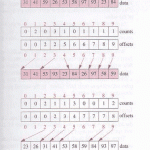
Sorting is the process of arranging elements in some logical order. Sorting methods are classified into the following categories: External sorting: This deals with sorting of data stored in external files. This method is used when the volume of data is very large and cannot be held in a computer’s RAM. Internal sorting: This deals with sorting of data held in the RAM of a computer. Sorting Methods The following are links to tutorials on some of the most popular sorting methods: Bubble sort Bucket sort Insertion sort Merge sort Read More
Hex Editor
A hex editor is a program edits compiled programs and binary data files. These editors are called hex editors because they most often present data in hexadecimal format. Hexadecimal is used because it is easier for most humans than working in binary. In addition, hexadecimal is frequently useful because computers tend to work with 8-bit bytes of information and because ASCII is an 8-bit code. Some hex editors are also able to edit raw disk partitions and other file system structures. Hex editors can sometimes be used to remove copy Read More
Java Virtual Machine
A Java Virtual Machine is quite simply a piece of software that enables Java technology to be recognized and successfully executed on a vast array of hardware platforms. Java virtual machines are so named because they provide a necessary environment for the Java bytecode to be executed. The flexibility of a JVM allows a Java applet to be written only once, but able to be run on virtually any operating system. Java virtual machines accept standardized binary format code. Java compilers translate this code into the necessary format needed before Read More
How to Check the Java Version

It is quite important to know which version of Java is presently installed on your computer. This might specially come handy to those who are developing applications and software on the Java platform. Using an outdated version of Java may hinder your Java development or even render web pages inappropriately in your browser. Mentioned below are few straightforward ways to check which version of Java is installed on your computer. Command Line Open Command Prompt and type in the following command: java -version Upon successful execution, the command will output Read More
Friend Function
The private data members of a class cannot be accessed by functions that are not a part of the class. The access to such members can only be given to the functions by specifying the function as friend of the class whose data structures are required by the function. In simple words, we can say that a friend function has an advantage of having an access to the private data members of the friend class. A function can be specified as a friend of a class by including its prototype Read More


Share on: