Steganography is the art and science of hiding messages. Steganography is often combined with cryptography so that even if the message is discovered it cannot be read. The word steganography is derived from the Greek words “steganos” and “graphein”, which mean “covered” and “writing.” Steganography, therefore, is covered writing. Historical stenganography involved techniques such as disappearing ink or microdots. Modern steganography involves hiding data in computer files. It is fairly easy to hide a secret message in a graphic file without obviously altering the visible appearance of that file. Steganography Read More
How a Smart Card Reader Works

Smart Card Readers are also known as card programmers (because they can write to a card), card terminals, card acceptance device (CAD), or an interface device (IFD). There is a slight difference between the card reader and the terminal. The term ‘reader’ is generally used to describe a unit that interfaces with a PC for the majority of its processing requirements. In contrast, a ‘terminal’ is a self-contained processing device. Smart cards are portable data cards that must communicate with another device to gain access to a display device or Read More
How to Reset a LinkSys Router Password
LinkSys is the division of the Cisco Company which manufactures some of the most widely used network routers in the world. The WRT54G, WRT160N, and WRT310N series are the most popular with the WRT54G being the first model deployed that supported third-party firmware. The current generation of LinkSys routers support the draft 802.11N wireless standard that provides an increased throughput of 270Mbit/s when communicating with other 802.11n compatible devices. As the capabilities of home networking devices have increased, so has the ability of the computers and mobile devices that consumers Read More
Antivirus Portable
With the many different viruses, worms, and Internet hacks that lay waiting around every virtual corner, users need stable antivirus software in order to combat these threats. Challenges may be met, however, when a user must combat viruses and other problems on multiple computers or even on mobile devices. Because of this, many software designers have created portable antivirus programs that can be transported from one computer to another by means of a USB flash drive or disc. This article will list a number of these portable antivirus programs that Read More
SMSS.exe
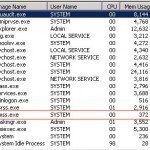
There are many processes that run behind the scenes in Windows operating systems. One of these processes that may look suspicious is the SMSS.exe. This is an execution file with the full name Session Management Subsystem. The Session Manager Subsystem is responsible for starting a session. When this process begins, the system thread is responsible for a number of specific tasks including launching the Winlogon, specific Win32 processes, and among other items, setting the system variables. Many computer users first notice the SMSS.exe process when a system shuts down abnormally. Read More
What is Tor?
Tor is a program that is able to hide the user’s online activities from third parties and prevent websites from seeing where the user is browsing from by rerouting the user’s sent and recieved data through the Tor Network. The Tor Network is made up of hundreds of volunteers from around the world that specifically setup their Tor client as a relay station for other users. Tor does have its downsides, however, as it blocks a number of browser plugins and it must be specifically configured for each application that Read More
What is HSPD-12?

Homeland Security Presidential Directive 12 (HSPD-12) is a presidential directive that President George W. Bush signed following the September 11, 2001 terrorist attacks. HSPD-12 required that all government agencies take measures to produce and distribute “smart cards” to their employees and contractors in order to properly identify those attempting to access federal buildings and computer networks. HSPD-12 was designed to reduce terrorist threats and improve federal security, although it has proven to be difficult to implement. How HSPD-12 Works HSPD-12 relies on smart cards to identify government employees and contractors. Read More
How to Remove Zlob

Also known as Troj/Zlob-QJ, the Zlob spyware trojan affects the Windows operating system. The trojan is activated once it has launched itself into a file and downloaded and installed from remote locations. Once installed, the spyware Zlob inputs malicious code into the system processes. Results from this spyware ranges from modifying data on the computer, deleting files off the computer, stealing information, causing malware, downloading code from the internet, and installing itself into the registry. Removing the Troj/Zlob-QJ is the same as removing any other trojans. Remember that trojans infects Read More
ISO 7816
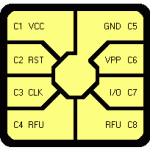
ISO 7816 is the internationally accepted standard for smart cards. ISO 7816 is a family of standards primarily dealing with aspects of smart card interoperability regarding communication characteristics, physical properties, and application identifiers of the implanted chip and data. The ISO 7816 family includes eleven parts which are in a constant state of flux as they are subject to revision and update. ANSI can be contacted to get the latest version of the 7816 standards. ISO 7816 Standards ISO 7816-1 The ISO 7816-1 standard specifies the physical characteristics of the Read More
How to Pick Locks

Learning how to pick locks is almost as much an art as it is a science. Locksmiths describe lock picking as the exploitation of a lock’s machinery to open a lock without a key. To understand the process of picking locks, the prospective picker has to be acquainted with how locks and keys function. The skill of picking a lock involves gaining a good feel for the lock mechanism and the technique needed to pick it. This requires practice and concentration. Locks are of many shapes and sizes, with many Read More


Share on: